In theory the best way to persuade people of the importance of correctly configuring (securing) the HTTP Security Response Headers on their websites is to create a narrative — a simple narrative.
One of the simplest would be, and sometimes in the security industry you’ll see mentions like this borne out of frustration: “this is incompetence!” or “the government doesn’t care about protecting your data!” or “the media is complicit!” or whatever.
None of those are correct.
Generally speaking most of the people involved with keeping government infrastructure safe really do care about the safety of those systems and the data they protect.
Most journalists care about facts, honesty, and truth. They want to get the story right, and they believe the public has the right to be informed.
The enemy is complexity.
Few Journalists are experts in the field of information security.
Information Systems is such an enormous field that most people working as programmers, systems administrators, webmasters, site reliability engineers, and many others, struggle to keep up with the rapid changes in their own field, and lack the time to keep up with all the security related challenges their system might face.
Keeping in mind that very nearly all of the people involved in these stories, staff, officials, and journalists, really do care about security, let’s take a look at some stories from the past couple years which illustrate that county governments are under attack, and that the consequences can be expensive, and potentially dire.
One thing you’ll notice as you read through these recent examples of county government infrastructure that’s been infiltrated, data stolen, and in some cases ransom extorted from the budgets of the counties, is that in the aftermath of these attacks the HTTP Security Response Headers of their websites weren’t correctly configured and probably weren’t audited. (If they had been, they would all be getting A or A+ scores).
How does this happen? There are several contributing factors.
People don’t realize how common cross-site scripting and other attacks against web-facing systems really are.
People don’t realize that HTTP Security Response Headers can protect against these attacks.
People don’t realize HTTP Security Response Headers exist.
Security audits don’t seem to require correct configuration of HTTP Security Response Headers.
People discover individual HTTP Security Response Headers, and set those, but don’t realize that the others exist.
There are other factors, too.
Let’s take a look at several county governments which were victims of ransomware, data exfiltration, or other cyber attacks within the past two years, and check to see if, in the aftermath of these incidents, they protected their web-facing infrastructure by correctly configuring their HTTP Security Response Headers.
I selected these basically at random from the first 30 search results for a simple phrase, something like: “county government cyber attacks”.
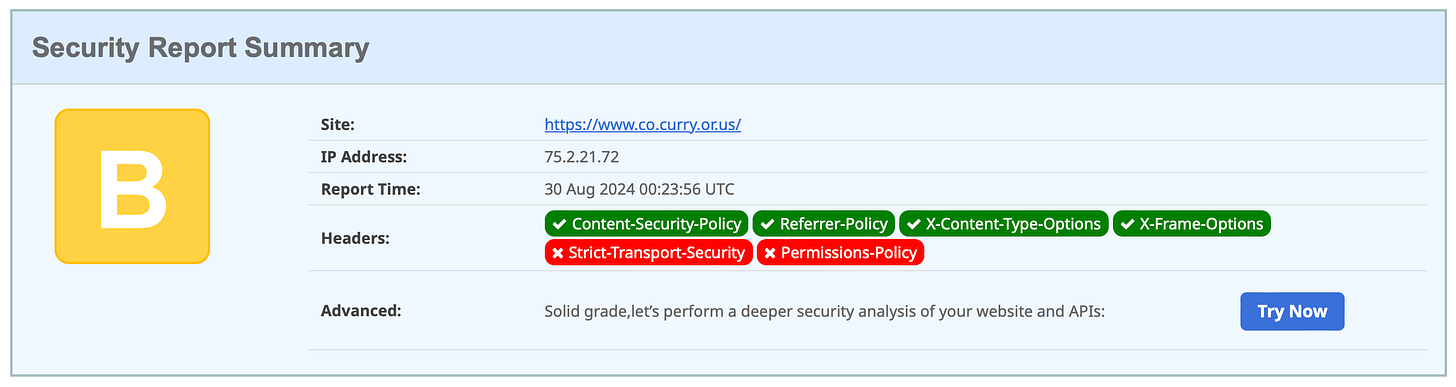
Curry County, Oregon (May 15, 2023)
Curry County (Oregon) computer system ‘starting from scratch’ after ransomware attack
“The county still has control over Tuesday’s election and over 911 dispatch calls. But Alcorn said the attack has affected every other part of county government operations.”
This county was attacked during the run-up to an election.
Counties manage many elections, not only the general elections that get lots of news coverage every other year, but also primaries and special elections to replace someone who vacated office early.
Still, these attacks might sometimes be targeted at counties during an election cycle, in order to try to capitalize on the extra stress in the system.
Is a county more likely to pay a ransom, if they’re in the middle of preparing for an election cycle?
You’ll catch me saying this again, and again, until they’re all fixed: failure to set “Strict Transport Security” should result in a failing grade, not a “B”.
Butler County, Pennsylvania (22 February 2024)
More than 6,500 people affected following Butler County cyberattack
According to county leaders, federal agents alerted them to "suspicious activity" on the computer network on Oct. 2, 2023. They opened an investigation, and solicitor, Julie Graham told KDKA on Feb. 21, 2024, they informed 6,748 people affected.
Graham said those potentially impacted were people "involved with county business and/or court or law enforcement matters, including some employees."
The data included social security numbers, driver's license numbers, passport numbers, and state identification numbers, among others.
…
In the meantime, they're in talks with the district attorney's office, and are working to prevent similar attacks in the future by taking steps like strengthening its network security.
At the Butler County, Pennsylvania website we see something that I’ll point out every time I notice it: for the love of Zeus, set Strict Transport Security. (Failure to set this should be an automatic grade of “F” no matter what else is correctly set.)
Shown in the full report (not in this screenshot is a warning worth taking a look at, if you’re the administrator of this site:
This policy contains 'unsafe-inline' which is dangerous in the script-src directive. This policy contains 'unsafe-eval' which is dangerous in the script-src directive.
It’s better to have an intentional Content Security Policy (CSP) set, than it is to leave it unset. However, organizations should recognize that these “unsafe” directives should be temporary placeholders. Whatever changes need be made to the website to arrive at a more strict CSP should be identified, and put into the work queue of the website development team as a security architecture work item.
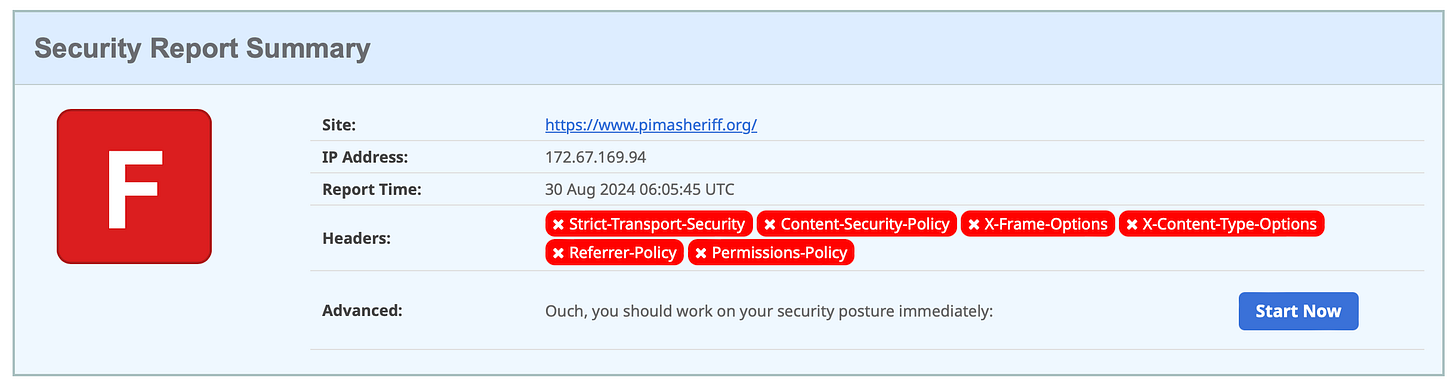
Pima County, Arizona (6 May 2024)
Pima County Sheriff Department explains cyber incident
Every once in a while, there’s a bit of good news! Here’s a nice story about a suspected cyber incident in which an active firewall system detected and prevented an intrusion.
The Pima County Sheriff’s Department says a recent cyber incident turned out to be a false alarm.
PCSD says its Information and Technology Division was alerted to a possible cyber-attack on the PCSD Public Information System Thursday, May 2.
PCSD says the Public Information System firewall detected this isolated incident and immediately blocked the attempted unauthorized access.
The investigation revealed no law enforcement data was compromised or released and the PCSD Information System firewall restricted access in the manner it was designed to.
This provides an opportunity to illustrate a common situation to keep an eye open for — organizations often have several or even many websites. HTTP Security Response Headers are configured independently for each website.
Here you can see that they’re not configured for the Sheriff department website, and are incompletely configured for the top level county website.
Washington County, Pennsylvania (15 February 2024)
Washington County pays nearly $350,000 in ransom to hackers
[Commissioner Nick Sherman voted ‘yes’ to pay the ransom. “I agree, nobody wanted to pay that. We don’t wake up to say, I’m excited to pay cyber terrorists in Russia.... that hacked our system.”
But Sherman explained the hackers stole more than social security numbers and driver’s license numbers.
Sherman explained it was more than leaked social security numbers that swayed his vote, but protecting children of the county from their information getting into the wrong hands.
“Some of the info they got was Children and Youth Services information about the children of Washington County... children in severe need of services, children who have been abused, abducted... very sensitive information,” said Sherman.
County leaders told Channel 11 that immediately after they paid the ransom the decryption key was delivered. The county is now 80% restored and back online.
Sherman called the hackers, “a highly skilled organization that goes across the world and hijacks information”.
“When you pay the ransom they go away, and they leave you alone, because they know if they don’t people will continue to not pay ransom. It’s a business model they follow.”]
Washington County officials indicated that ransom was paid to “Russian hackers”.
There are at least two Advanced Persistent Threat (APT) groups which appear to be affiliated with the Russian state, one with the intelligence service, one with the military. However, this incident may have been one of the several freelance, loosely organized criminal gangs, or an independent operator.
It’s important to keep in mind that, outside of Russia there exist multiple state-backed hacker groups including from North Korea, China, and Iran, as well as many organized criminal gangs extracting ransom in the world, not only the one group that infiltrated your network and systems. When those other groups see that an organization was vulnerable, was successfully attacked, and paid the ransom, they may be attracted to that juicy target.
Sometimes they don’t provide the decryption key.
Sometimes their software has defects and the decryption key doesn’t work.
Some are “small time” criminals, not playing the long game. They might be interested in a few quick hits and might not care or have thought about the long term strategy. In other words, they might take the money and run.
It’s very common in these public statements to refer to the malicious hackers as “highly skilled” which some of them might be. However, this phrase is intended to provide cover to organizations that are embarrassed that they were victimized. Some hackers are derisively referred to as “script kiddies” because they’re not considered as “highly skilled” by the highly skilled hackers. They specialize in tricking people into handing over passwords, or exploiting well-known cross-site scripting attacks using programs written by others, and then escalating privilege once inside the system. Viewed another way, they’re highly skilled, but at different things than you think, and they’re sometimes exploiting weaknesses which should have been protected.
The first HTTP Security Response Header that you set should definitely be Strict Transport Security, but it shouldn’t be the last.
Once your systems have been attacked successfully, and particularly if ransom has been paid, extra care should be taken to secure the network and systems to prevent future attacks. The honor among these thieves, to the extent that there’s any at all, doesn’t extend to the other people engaged in this vicious business.
Waupaca County, Wisconsin, Schools (4 June, 2024)
Waupaca Computer System Hacked
NOTE: This 👆🏼 article also has an interesting discussion of the Minneapolis schools hack.
[The next day on May 31… the school’s system analyst, sent an email to the parents of the students:
“We are writing to notify you of a recent event that impacted our school district’s network systems. On May 13, 2024, the district became aware of suspicious activity causing a disruption within our computer network. The district immediately began an investigation with the assistance of third-party cyber security and network specialists to determine the nature and scope of the activity, confirm its impact on our systems, and to restore functionality to our network. We also provided notice to federal law enforcement as well as relevant state regulators, as required. Through the investigation, we determined that an unauthorized actor did gain access to our network causing the service disruption. Further, we confirmed that no student or parent information was impacted by this event.
We take the confidentiality, privacy, and security of information in our care seriously. As part of this ongoing commitment, we are reviewing our existing policies and procedures, and implementing additional technical safeguards. Throughout this disruption, our building entrances remained secure and we were able to continue with in-person learning.
While our technology networks and security systems are up to date, unfortunate events like this happen. And while our desire was to communicate this information to families sooner, protecting the integrity of the investigation limited us in sharing information.”
Soft-target schools
Ransomware attacks are one the rise in Wisconsin and across the nation. The school districts of Janesville, Neenah, Middleton, Kenosha, Elmbrook, Adams-Friendship and Tigerton have been hacked.]
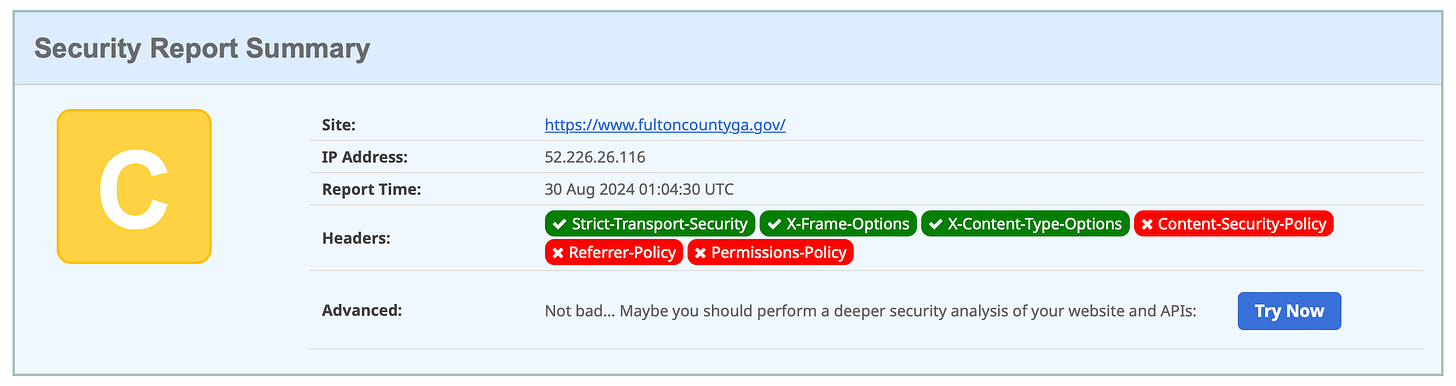
Fulton County, Georgia (30 January 2024)
This incident generated more pubic interest than normal. I’ll quote here from two of the many articles about this incident.
Georgia’s Fulton county hacked, but DA says Trump election case is unaffected
[Fulton county, which includes most of Atlanta, was experiencing a “widespread system outage” from a “cybersecurity incident”, the chair of the county commission, Robb Pitts, said on Monday in a video posted on social media. Notably, he said, the outage is affecting the county’s phone, court and tax systems.]
Georgia's Largest County Is Still Repairing Damage From January Cyberattack
1 March 2024
Another possibility is that LockBit lost access to stolen data in the disruption by law enforcement, ransomware analyst Brett Callow of the cybersecurity firm Emsisoft said in a post on X, formerly Twitter.
LockBit is believed to have extracted $120 million from thousands of victims since it began operating in 2019. It accounted for 23% of the nearly 4,000 attacks globally last year in which ransomware gangs posted stolen data to extort payment, according to cybersecurity firm Palo Alto Networks.
Cybersecurity experts believe LockBit as a brand may now be in its death throes -- but could easily re-emerge rebranded under a new name with the same core members, as happened with previous ransomware groups that came under intense law enforcement pressure.
LockBit and other ransomware syndicates are compartmentalized operations. Outside the core group that rents out the malware and maintains the infection infrastructure are so-called affiliates who manage the hacking, malware activation and negotiations and get the bulk of the profits.
In Fulton County, officials reported widespread disruptions following the cyberattack the weekend of Jan. 27. County police couldn't produce incident reports and the sheriff's office had to fall back on paper forms to process jail detainees. Residents couldn't pay county utility bills online or use the internet to access property records. Clerks were unable to issue marriage certificates and firearm permits.
Organized criminal gangs like LockBit may not be directly affiliated with a sponsoring state, but they do benefit directly. The Russian authorities look the other way, so long as these groups don’t target Russian government or business interests.
I suspect that the level of cyber attacks directed at Fulton County are higher than typically seen for other counties in the United States, making it all the more important to better protect their web-facing infrastructure.
Douglas County, Colorado (January 22, 2024)
Douglas County Libraries hacked by overseas criminal group
[It's not clear how the hackers got into the system. Pasicznyuk says the library recently had a cybersecurity audit and received an A+ rating. Luckily, the library has cybersecurity insurance, and they're working with a cybersecurity firm to recover from the hack.]
This example illustrates how security audits run by professionals with expertise and experience in the field can overlook something.
I’ve noticed that organizations conducting SOC2 compliance audits (typically technology startups that have venture capital backing) are more likely to recommend correct configuration of HTTP Security Response Headers. I’m not sure why this hasn’t yet spread as a requirement for other types of security audits.
Kent County, Delaware (12 July 2023)
Delaware county struggling to respond to cyberattack
As of Wednesday afternoon, county websites and phone numbers were unresponsive. The governor's office and Dover city officials did not respond to requests for comment. In the county statement, they said they will only release “limited details” because the issue is being investigated by law enforcement.
Officials did not respond to requests for comment about whether ransomware is involved, but 2023 has seen dozens of attacks on local governments by gangs seeking to extort poorly-resourced municipal bodies.
Counties across the U.S. — including ones in California, South Carolina, New Jersey and Oregon — have been attacked this year alongside major metropolitan areas like Oakland and Dallas.
On Monday, Hayward, California said it was forced to shut off its website and several online municipal portals in response to a cyberattack.
A great many security consulting companies have posted advice to the web about how to protect against cross-site scripting attacks. The advice tends to be a laundry list of things that programmers of web-facing apps should do, such as validate input when accepting user input in forms.
I’ve yet to find one that recommends correctly setting the HTTP Security Response Headers.
The problem is that due to the nature of complex modern web-facing software it’s probably not even possible to correct all of defects in web-facing software.
HTTP Security Response Headers are designed to allow better protection against injection attacks and other attacks, even when the software running on the website has undiscovered defects within it.
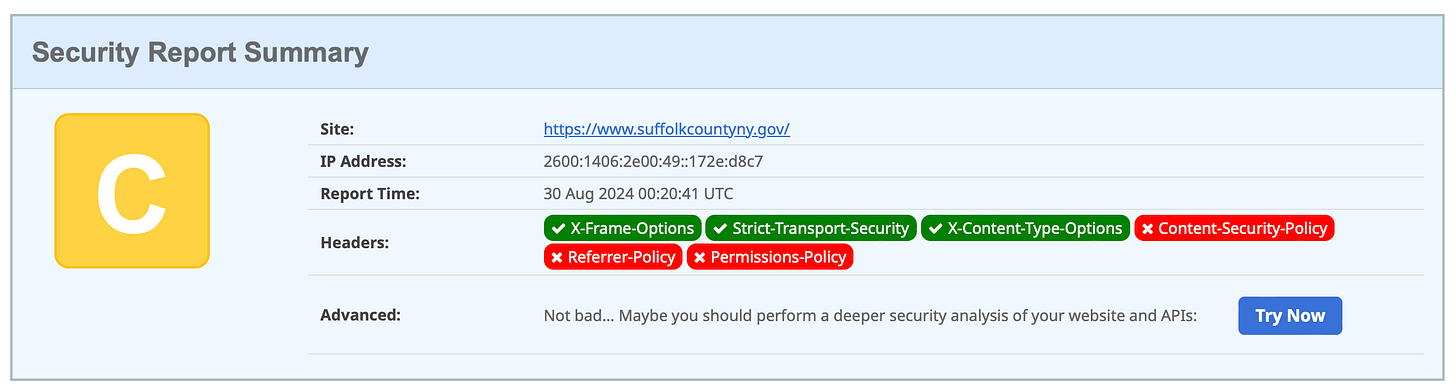
Suffolk County, New York (November 28, 2022)
How a Cyberattack Plunged a Long Island County Into the 1990s
[Emergency dispatchers taking down 911 calls by hand, unable to use their geolocation technology for callers. Police officers radioing in crime scene details, rather than emailing reports to headquarters. Office workers resorting to fax machines.
For weeks this fall, the government of Suffolk County was plunged back into the 1990s after a malicious ransomware attack forced it largely offline. A frantic push to counter the threat hobbled the county, as officials disabled email for all 10,000 civil service workers and scrubbed infected hardware, seeking to stem fallout from compromised computer systems.
More than two months after the attack, some of the gears that run much of Long Island are still stubbornly mired in a cybermorass. It is a situation that experts say not only reveals the county’s vulnerability but also presents an ominous warning for a nation unprepared for crippling online threats.]
It’s very likely that a county government which experienced a cyber attack leading to major service outages and many weeks of cleanup efforts would want to prevent that from happening, again.
Suffolk County could improve their security posture by following the recipe for correctly configuring their HTTP Security Response Headers (see the “Resources” section below).
Resources
If you want to check your website to see the status of your HTTP Security Response Headers, there are several free online tools. The one used in the screenshots in the article above is:
SecurityHeaders.com by Probely
If you’re ready to secure your website, here’s the recipe you need:
Recipe for Securing Your Website with HTTP Security Response Headers
















Share this post