Secure the Vote
can we do this in 42 days (six weeks)?
As I write this there are 83 days and a few minutes to go, until Election Day in the United States of America and I’ve discovered something I don’t like, and you won’t like, either.
The public-facing websites of most of the state and county government websites, and also those of the major political parties and campaigns, have poor security configuration of a type known as Security Headers.
These configuration settings protect against several types of common attacks against websites.
Why should you care?
Primary and general elections in the United States of America 🇺🇸 involve all 50 (fifty) state governments, over 3,000 (three-thousand) county governments, dozens of political party organizations at the state level, and thousands of candidates at federal, state, and local levels.
In elections going back over a decade many of these organizations are under attack from increasingly sophisticated adversaries, hostile to the interests of the United States — even your local candidates and county governments.
As recently as yesterday, headlines broke about recent attempt to break into the information systems of both candidates for POTUS — one of which was successful and resulted in the leaking of confidential information.
The information systems of candidates, governments, and political parties are attacked in the same ways that businesses are attacked. The major breaches of cyber security include:
🟤 weak passwords,
🟤 phishing, and
🟤 cross-site scripting.
Security headers protect against cross-site scripting and other weaknesses sometimes used as part of phishing attacks.
The Good, The Bad, and the Ugly
The good news is that it’s not very difficult to put these basic protections in place for a website. You can take a website from an “F” to a “C” in a few minutes, to a “A” in a few hours usually, and to an “A+” in a few days.
The bad news is that there are thousands of websites that need to be tuned-up, and they’re maintained by thousands of different people. Most of those people are busy and their managers don’t realize this should be a priority for the team.
The ugly news is that every one of these websites, state and county governments, campaigns and candidates, and political parties, may be under attack this election cycle.
Let’s Work Together to Put This Shield in Place
The reason this problem hasn’t been fixed already is because nobody in the security and information systems ecosystem has figured out how to make money fixing this problem.
It occurred to me that if I described this problem, maybe public pressure could result in the problem being fixed.
In the resources below is a link to a simple online tool that you can use to inspect the “Security Response Headers” of the website of your county or state government website. Please do that, and when you see that the grade is anything less than an “A” please contact the relevant government officials. For counties that’s probably the county commissioner. For states it might be the CIO.
I plan to keep writing about this problem until it’s fixed.
If enough people share this information widely, check the websites of their state and county government agencies, and believe that better information security is good for America, we can fix this problem before people start voting.
Let’s get this fixed in 42 days, by Tuesday September 24, 2024.
Together we can do this.
Information security is national security.
Let’s Look at Some Report Cards
To get started, let’s take a look at a few examples, including the websites of the candidates for President, a state government (Montana because I happen to live here), a county government (Missoula County), and the state political party websites for the Republican Party, Democratic Party, and Green Party of Montana.
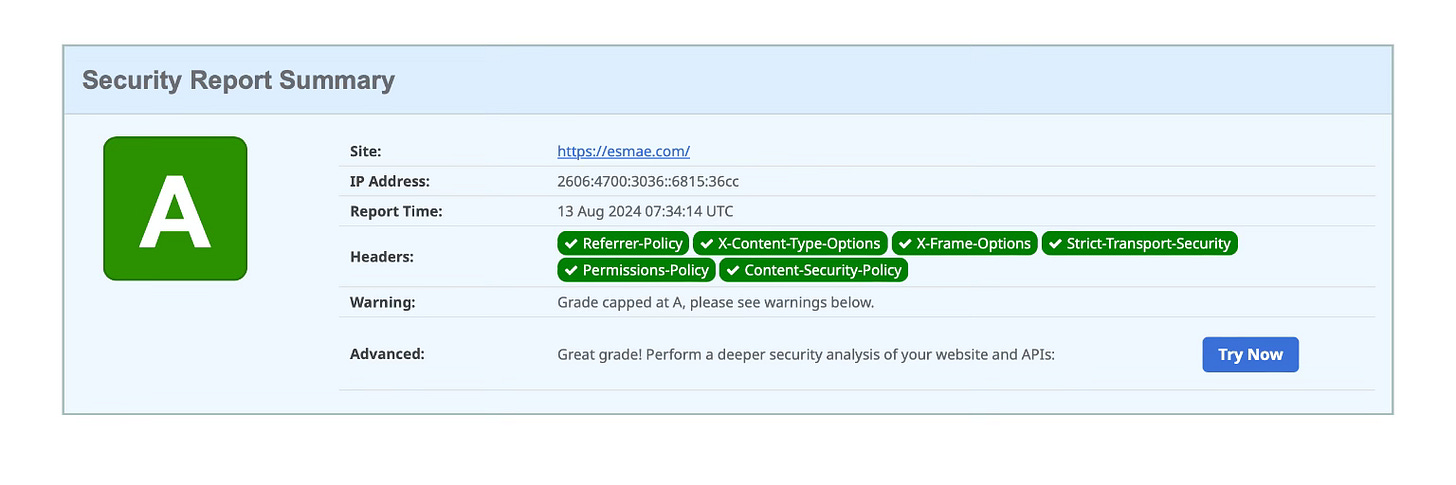
First, though, let me show you what a grade of “A” looks like, because I haven’t yet found one in all the election related websites that I’ve looked at. A couple years ago I set up a site to host a demo for a software product called Esmae, and configured the security response headers.
Notice the warning about a setting which prevents the site from getting the top “A+” rating — the site uses “unsafe hashes” in the CSP (Content Security Policy). Getting from an “A” to an “A+” for most websites isn’t particularly difficult, but it’s very fussy. We’ll talk more about this sometime later, but the world needs a special tool to make this easier, I just haven’t been paid to build that tool, yet. One step at a time.
Now that you see what a high score (it could be better!) looks like, let’s look at some election related sites.
States
The Montana.gov website at present sports no security response headers and receives an “F” score. Plucking the low hanging fruit can boost the score of this site to a “C” or even a “B” pretty easily. I’d be happy to help with that if someone can put me in touch with the right people.
State governments can be quite large and in some states the “state government website” might actually be dozens or maybe even hundreds of different websites, each of which should be checked for a security tune-up.
Counties
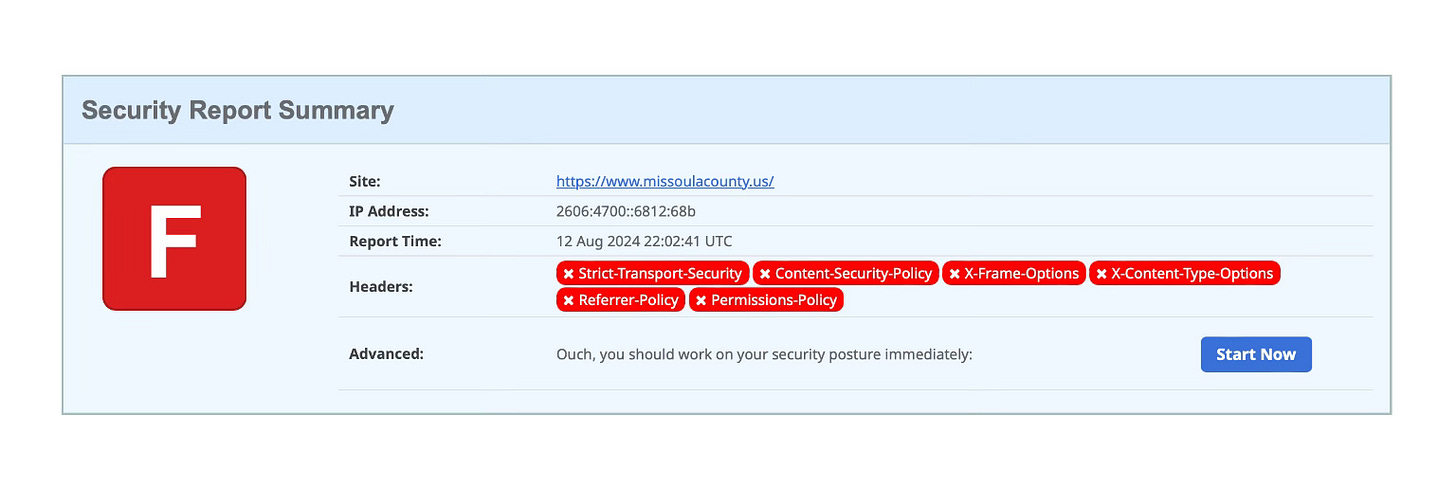
We’ll take a look at the website for Missoula County Montana, since that’s where I live. No security response headers are set of this website which currently gets a grade of “F”. Getting to a “C” or even a “B” is pretty easy. I’ve already reached out to our County Commissioners to help them understand the importance of better security for county websites and to get in touch with the right people to improve this score.
Campaigns
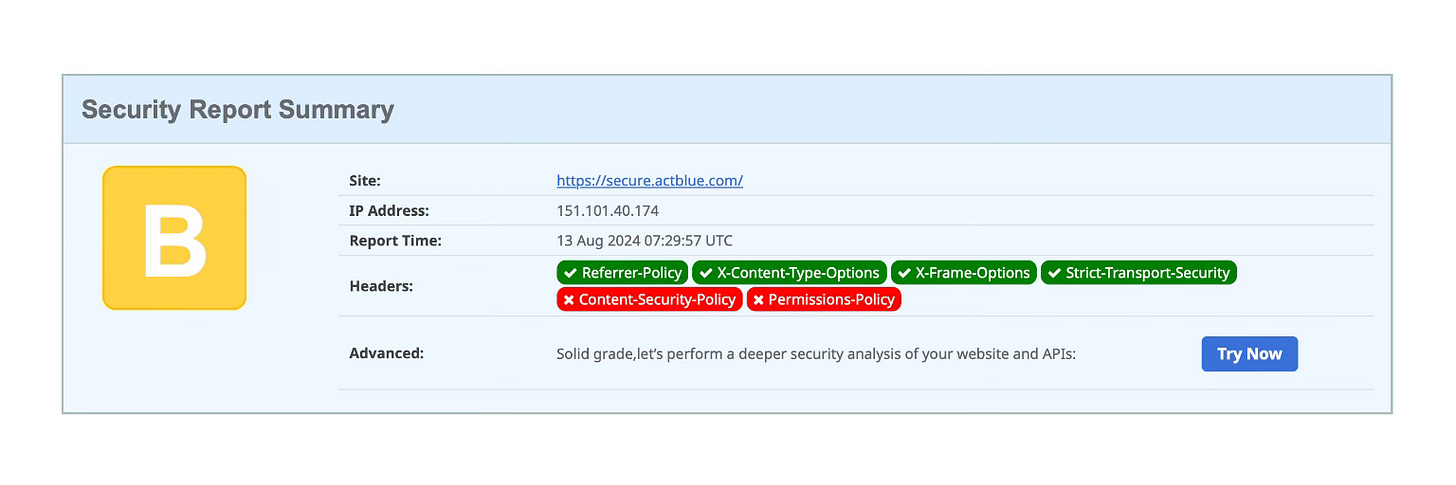
The website for the Kamala Harris campaign presently scores a grade of “F” with no security response headers set. Donation buttons link to the Act Blue website which gets a better score of “B”.
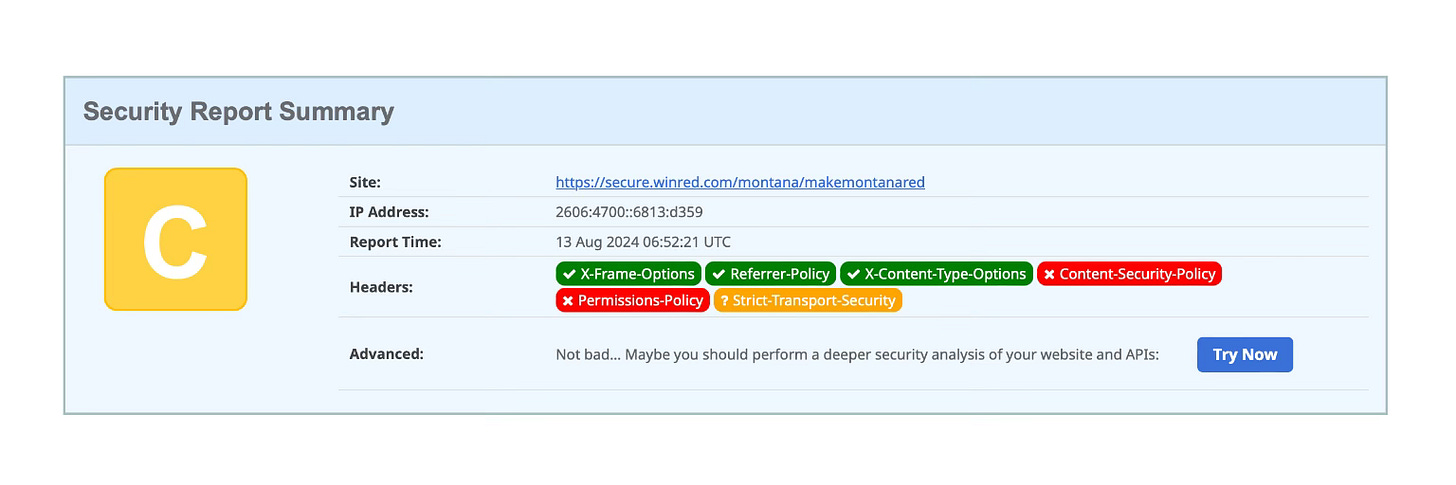
The website for the Donald Trump campaign presently is redirected to a special landing page hosted on the winred.com site and scores a “C”. Fixing the timeout issue for the strict transport security at winred.com would probably get this site to a “B”.
Parties
Let’s take a look at a few of the political party websites in Montana.
Political parties aren’t counting your vote, but they are communicating with voters and manage a great deal of identity and contact related information. They also often take donations at their websites and process payments including recurring donations. Political parties also have lots of confident internal communications regarding their plans and strategies.
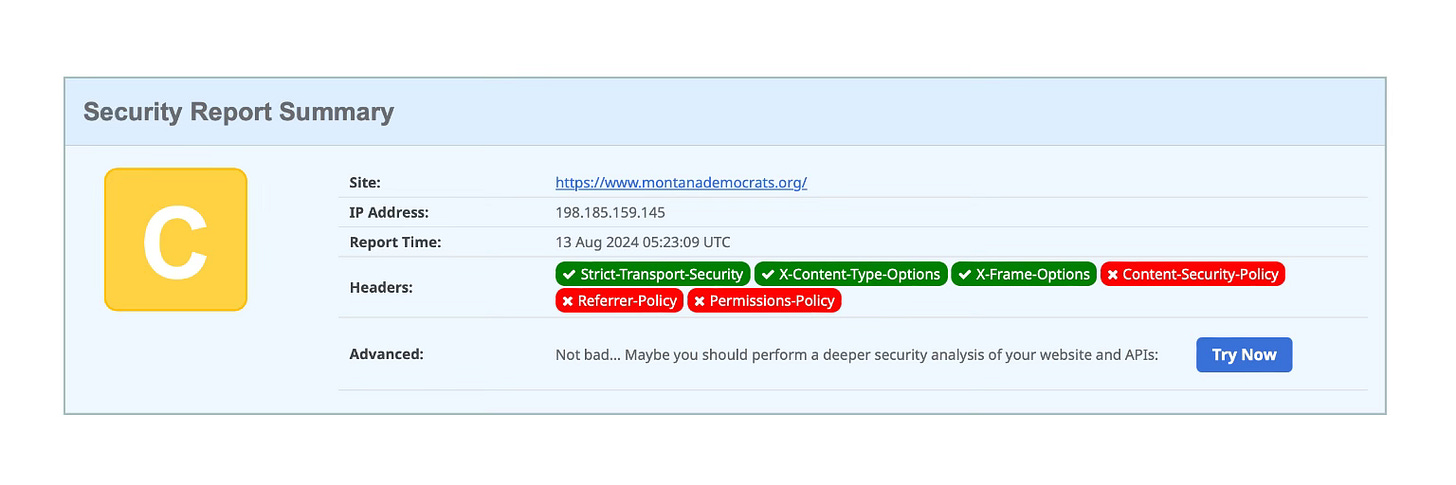
The website of the Montana Democrats presently scores a “C” grade which means that it sets several of the basic security headers including the Strict Transport Security. It doesn’t set the ones that are a little more complex. This is a good example of how to capture the low-hanging fruit. You can set several basic security headers pretty quickly without much risk. Every site that has a grade of “D” or “F” could get to a grade of “C” within a day.
The website of the Montana GOP doesn’t set any security headers on their top level website (the “front door” if you will) but I noticed that they set a few on the auxiliary website where they collect donations — albeit one of them (a timeout value for strict transport security) is set to a value considered to be too short, and out of compliance with recommendations. They could get both of these to a solid C in a few minutes (I’m happy to help.)
It’s very common for the brochure website to be configured differently from the part of the website that takes donations, so be sure to check both URLs if you’re a webmaster working to improve your security response headers.
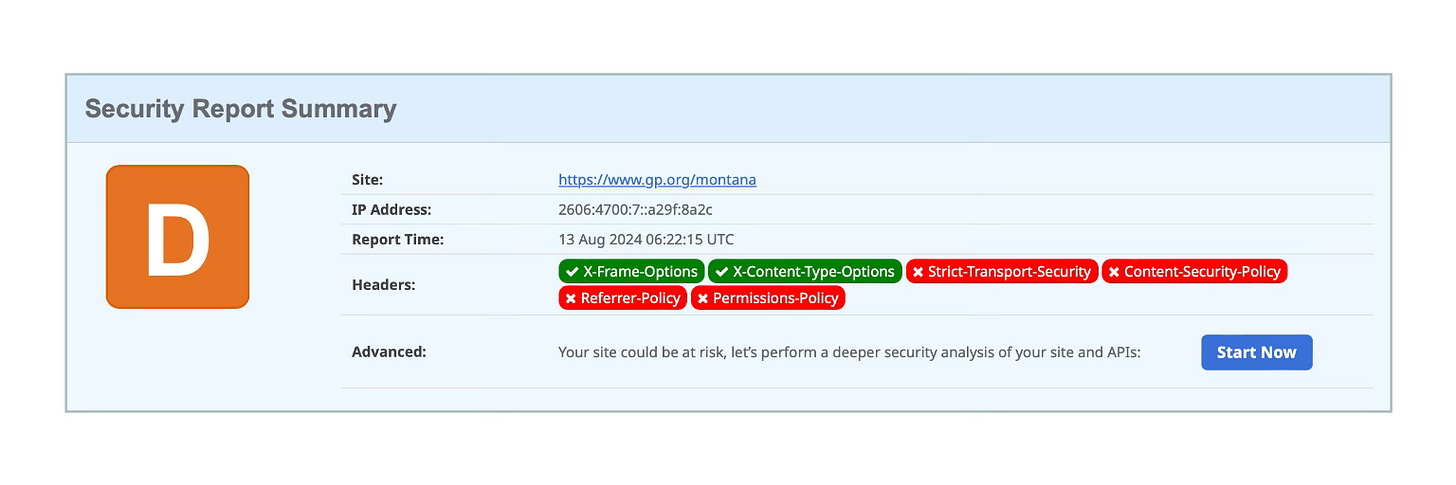
The Montana Green Party website currently gets a “D” grade and only sets a few security headers. Their donation site seems to be hosted on the same server and has identical security headers configuration to the top level site.
It appears the Montana Green Party site is hosted on the same web server as the Green Party websites for the Green Parties of the other states. If so, the Green Party could improve the security response headers for all of their state party websites at once.
The Montana Libertarian Party website currently gets a “D”. Notice that they, too, set the max-age for strict transport security to a value considered too short and out of compliance (recommended is 30 days). Their donation appear to be hosted on the same server and have the same configurations for security headers.
We all know the United States of America are 50 (fifty) in number, but did you know there are 3,143 (three-thousand one-hundred and forty-three) counties in the USA?
Generally speaking but especially if you live in a “swing state” you very much want your elections apparatus to be both trusted and trustworthy — for state, county, and local city governments.
Contact your political party, state, county, and candidates and ask them to tune up their security response headers to protect their websites, data, voters, and country.
Resources
OWASP — HTTP Security Response Headers Cheat Sheet
SecurityHeaders.com powered by Probely (I’m not affiliated with Probely, they just make one of the best free tools for checking security response headers).